DNS over HTTPS (DoH) is a protocol for performing remote Domain Name System (DNS) resolution via the HTTPS protocol. A goal of the method is to increase user privacy and security by preventing eavesdropping and manipulation of DNS data by man-in-the-middle attacks by using the HTTPS protocol to encrypt the data between the DoH client and the DoH-based DNS resolver.
An alternative to DoH is the DNS over TLS (DoT) protocol, a similar standard for encrypting DNS queries, differing only in the methods used for encryption and delivery. On the basis of privacy and security, whether or not a superior protocol exists among the two is a matter of controversial debate, while others argue the merits of either depend on the specific use case.
DoH improves privacy by hiding domain name lookups from someone lurking on public WiFi, your ISP, or anyone else on your local network. DoH, when enabled, ensures that your ISP cannot collect and sell personal information related to your browsing behavior.
- Some individuals and organizations rely on DNS to block malware, enable parental controls, or filter your browser’s access to websites. When enabled, DoH bypasses your local DNS resolver and defeats these special policies. When enabling DoH by default for users, Firefox allows users (via settings) and organizations (via enterprise policies and a canary domain lookup) to disable DoH when it interferes with a preferred policy.
- In the US, Firefox by default directs DoH queries to DNS servers that are operated by CloudFlare, meaning that CloudFlare has the ability to see users' queries. Mozilla has a strong Trusted Recursive Resolver (TRR) policy in place that forbids CloudFlare or any other DoH partner from collecting personal identifying information. To mitigate this risk, our partners are contractually bound to adhere to this policy.
- DoH could be slower than traditional DNS queries, but in testing we found that the impact is minimal and in many cases DoH is faster.
How To Enable DNS over HTTPS in Browser
DNS over HTTPS in Firefox is enabled by default for its users in the US. Again, the feature relies on third-party DNS servers that support DoH such as Cloudfare, NextDNS etc.
Mozilla Firefox users outside of the US can enable the DoH by going to browser preferences > General Tab > Network Settings > Settings > Enable Enable DNS over HTTPS.
Starting with Chrome, Google by default uses DNS over HTTPS protocol. Users will find the Chrome DoH settings under Settings > Privacy and Security > Security > Under the Advanced section.
Here users have the option to choose Google Chrome’s built-in DoH or use a custom DNS server that supports DoH. The same settings are also available on Google Chrome for Android.
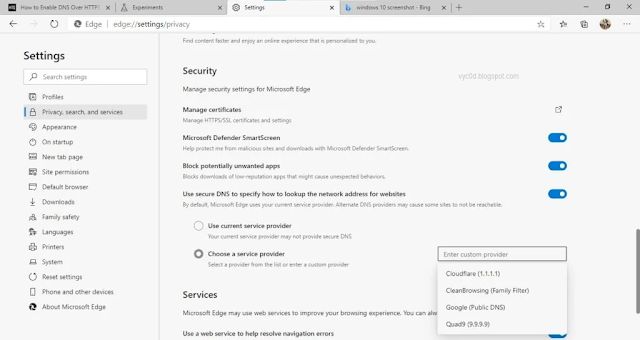
Microsoft also supports “secure DNS” protocol. However, Microsoft Edge won’t use DoH until a the user has selected a DNS provider that supports DoH. DNS over HTTPS settings in Edge are located in Settings > Privacy, search, and services > Under the security section.



Comments